Hello Freelancer, Get the DOT NET 3.5 USING C# TEST of Latest version 2018. We are ready here to provide your desire upwork test answer. We already tested all exam test information Available include on here. So Dear, Why Late? Read the below full exam test and get more information from our website.
1. Which of the following are static methods of the System.Reflection Activator class? Answers:
- CreateComInstanceFrom<
- CreateInstanceFrom
- GetInstance
- CreateInstance
- All of the above
2. Which of the following are true about Extension methods? Answers:
- They must be declared static
- They can be declared either static or instance members
- They must be declared in the same assembly (but may be in different source files)
- Extension methods can be used to override existing instance methods
- Extension methods with the same signature for the same class may be declared in multiple namespaces without causing compilation errors
3. When using a DataReader to access the results of a Database operation, which of the following are true? Answers:
- The DataReader provides a cursor that can be used to move forward and backwards through the result.
- The DataReader provides random access capabilities on the result.
- The Application code can reference the first row of a multi-row result set faster than it can be by loading it directly into a DataTable
- The DataReader can provide the Schema of the result to the application code.
4. Which of the following scenarios are applicable to Window Workflow Foundation? Answers:
- Document-centric workflows
- Human workflows
- User-interface page flows
- Builtin support for communications across multiple applications and/or platforms
5. Which of the following are true about using ADO.NET DataSets and DataTables? Answers:
- The connection to the database must remain valid for the life of the data objects
- All tables in a dataset must come from the same database.
- A given instance of a DataTable can be in only one DataSet
- Changes made to multiple tables within a DataSet can easily be transferred to a new DataSet which contains only the changes
- Content from multiple DataSets can easily be combined into a single DataSet that contains the net result of all changes.
6. Which of the following are true with respect to the standard implementation of Garbage Collection? Answers:
- Objects must be set to null in order to be eligible for garbage collection
- Unless specific steps are taken, an object may be moved in memory
- Objects become eligible for garbage collection as soon as it is impossible for any code to access them
- Objects which implement finalizers will always have the finalizer called at some point
7. Which of the following types guarantee atomic reads and writes? Answers:
- int
- double
- string
- long
- float
8. Which of the following does using Initializer Syntax with a collection as shown below require? CollectionClass numbers = new CollectionClass { 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 }; Answers:
- The Collection Class must implement System.Collections.Generic.ICollection<T>
- The Collection Class must implement System.Collections.Generic.IList<T>
- Each of the Items in the Initializer List will be passed to the Add<T>(T item) method
- The items in the initializer will be treated as an IEnumerable<T> and passed to the collection constructor+K110
9. Which features that are not supported in the System.TimeZone class does the System.TimeZoneInfo class provide? Answers:
- It provides readable names for both regular time and, if appropriate, daylight savings time
- It provides a means of enumerating the known time zones that are available on the local system
- It provides functionality to create custom time zones
- It provides the period the time zone was in effect for. For example: From 1986 to 2006, it was observed from the first Sunday in April to the last Sunday in October, but since 2007, it is being observed from the second Sunday in March to the first Sunday in November
10. Within Windows Workflow Foundation, Compensating Actions are used for: Answers:
- provide a means to rollback a failed transaction
- provide a means to undo a successfully committed transaction later
- provide a means to terminate an in process transaction
- achieve load balancing by adapting to the current activity
11. Of which elements does Generics allow parameterization by type?Answers:
- Classes
- Structs
- Methods
- Events
- Fields
12. Which of the following do the advantages of Lambda Expressions over Anonymous methods include? Answers:
- More concise syntax
- The types for a Lambda Expression may be omitted
- The body of an anonymous method can not be an expression
- Lambda Expressions permit deferred type interference, that anonymous methods do not
- All of the above
13. In which of the following types of applications can Windows Workflow Foundation be used? Answers:
- Console Applications
- Windows Forms based Applications
- Windows Presentation Foundation based Applications
- ASP.NET based applications
- All of the above
14. Which of the following items are recommended when using XML comments to generate documentation? Answers:
- <exception>
- <code>
- <summary>
- <events>
15. With which class is the task of mapping a specific point in time into units, such as weeks, months, and years accomplished? Answers:
- System.DateTime
- System.TimeSpan
- System.Globalization.Calendar
- System.Globalization.CultureInfo
16. Which of the following are true regarding the System.Collections.Generic.HashSet<T> class? Answers:
- HashSet is an unordered collection.
- HashSet requires that each element be unique as determined by either a supplied EqualityComparer or the default EqualityComparer
- Operations on sets (Union, Intersection, etc) always create new result sets
- HashSet provides functionality for “conceptual sets” where the rules for membership can be specified without actually creating all of the items.
17. Which of the following are true regarding System.Threading.ReaderWriterLockSlim? Answers:
- It is optimized for single processor/core operations
- It is optimized for usage where writes from multiple sources are common
- A thread which has a read lock on a resource may not acquire a write lock on the same resource
- By default, a thread which has a read lock on a resource and attempts to get another read lock on the same resource will throw an exception
18. The framework provides three different timer classes. Select the answer that properly matches the class with the listed characteristic. Answers:
- System.Threading.Timer Simple timer which requires a delegate to be supplied for execution when the timer expires. execution of the method provided by the delegate will be invoked on a ThreadPool Thread.
- System.Timers.Timer: Designed for use with worker threads in a multithreaded environment. Can move among threads to handle the raised Elapsed event May result in more accuracy than System.Windows.Forms.Timer instances.
- System.Windows.Forms.Timer Lower Resolution timer which requires a UI message pump on the creating thread.
- All of the above
19. Which of the following advantages does System.Collections.IDictionaryEnumerator provide over System.Collections.IEnumerator? Answers:
- It adds properties for direct access to both the Key and the Value
- It is optimized to handle the structure of a Dictionary.
- It provides properties to determine if the Dictionary is enumerated in Key or Value order
- It provides reverse lookup methods to distinguish a Key from a specific Value
20. While using the capabilities supplied by the System.Messaging classes, which of the following are true? Answers:
- Information must be explicitly converted to/from a byte stream before it uses the MessageQueue class
- Invoking the MessageQueue.Send member defaults to using the System.Messaging.XmlMessageFormatter to serialize the object.
- Objects must be XMLSerializable in order to be transferred over a MessageQueue instance.
- The first entry in a MessageQueue must be removed from the queue before the next entry can be accessed
- Entries removed from a MessageQueue within the scope of a transaction, will be pushed back into the front of the queue if the transaction fails.
21. What impact will using implicitly typed local variables as in the following example have? var sample = “Hello World”; Answers:
- The actual type is determined at compilation time, and has no impact on the runtime
- The actual type is determined at runtime, and late binding takes effect
- The actual type is based on the native VARIANT concept, and no binding to a specific type takes place.
- “var” itself is a specific type defined by the framework, and no special binding takes place
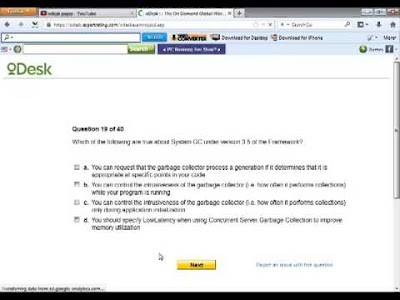
22. Which of the following are true about System.GC under version 3.5 of the Framework? Answers:
- You can request that the garbage collector process a generation if it determines that it is appropriate at specific points in your code
- You can control the intrusiveness of the garbage collector (i.e. how often it performs collections) while your program is running
- You can control the intrusiveness of the garbage collector (i.e. how often it performs collections) only during application initialization
- You should specify LowLatency when using Concurrent Server Garbage Collection to improve memory utilization
23. Which of the following operators can be overloaded? Answers:
- Assignment (=)
- Conditional (&&,||)
- Logical (&,|,^)
- Shift (<<, >>)
24. Which of the following does the System.IO.Pipes namespace provide?Answers:
- Interprocess communication through anonymous and/or named pipes.
- Access to named pipes using System.IO.Stream
- Access to system level pipe security implemented as discretionary access control lists (DACL) and/or system access control lists (SACL),
- Asynchronous read and write operations
- All of the above
25. Which of the following statements do Expression Trees fit best? Answers:
- Expression trees are a data structure which can be initially composed using language syntax.
- Expression trees are dynamically generated code which is executed to perform the desired function.
- Expression trees can only be created from Lambda Expressions
- Expression trees can be modified once they are created
- All of the Above
26. By which contract are the ws-addressing action and replyaction elements of the soap envelop controllable when Windows Communication Foundation is used? Answers:
- ServiceContract
- OperationContract
- DataContract
- MessageContract
27. Which of the following are true when comparing ADO.NET with Microsoft DNA (Distributed interNet Applications)? Answers:
- ADO.NET provides significantly better performance.
- ADO.NET is better suited for communications between disparate systems/applications.
- ADO.NET can eliminate the need for COM components in the communication layer.
- DNA makes it easier to communicate across firewalled boundaries.
28. When Deleting a DataRow from the DataRowCollection of a DataTable, you can: Answers:
- use the DataRowCollection.Remove method to immediately delete the row.
- use the DataRowCollection.Remove method to mark the row for deletion when DataRow.AcceptChanges is called.
- use the DataRow.Delete method to immediately delete the row.
- use the DataRow.Delete method to mark the row for deletion when DataRowAcceptChanges is called.
29. Which of the following are required to be true by objects which are going to be used as keys in a System.Collections.HashTable? Answers:
- They must handle case-sensitivity identically in both the GetHashCode() and Equals() methods.
- Key objects must be immutable for the duration they are used within a HashTable.
- Get HashCode() must be overridden to provide the same result, given the same parameters, regardless of reference equalityl unless the HashTable constructor is provided with an IEqualityComparer parameter.
- Each Element in a HashTable is stored as a Key/Value pair of the type System.Collections.DictionaryElement
- Allof the above
30. Which of the following are goals of Windows Communication Foundation?Answers:
- Bringing various existing communication technologies into a unified environment.
- Cross vendor/platform communication.
- Support for asynchronous communications.
- Support for distributed applications based on technologies such as MSMQ and/or COM+
- All of the above
31. Which access limitation is found in a class member declared protected internal? Answers:
- Access is limited to the containing class plus any classes derived from the containing class
- Access is limited to the current assembly
- Access is limited to the containing class plus any classes derived from the containing class that are also in the current assembly
- Access is limited to the containing class plus any classes derived from the containing class or any other class in the current assembly
32. When Windows Communication Foundation is used to develop a Web Service, which of the following are supported? Answers:
- WS-Addressing
- WS-MetadataExchange
- WS-Security
- WS-Atomic Transaction
- All of the above
33. To which contract is the SessionMode property to disallow, require, or permit applied when Windows Communication Foundation is used? Answers:
- ServiceContract
- OperationContract
- DataContract
- MessageContract
34. Which of the following is not supported by remoting object types?Answers:
- well-known singleton
- well-known single call
- client activated
- context-agile
35. The default number of threads per processor in the System.Threading.ThreadPool class under version 3.5 of the Framework is:Answers:
- 1
- 25
- 250
- 100
- 500
36. To which of the following can System.IO.IsolatedStorage not be scoped?Answers:
- Restricted to a Specific Application
- Restricted to a Specific AppDomain
- Restricted to a Specific User
- Restricted to a specific Physical Media
37. When using an automatic property, which of the following statements is true? Answers:
- The compiler generates a backing field that is completely inaccessible from the application code.
- The compiler generates a backing field that is a private instance member with a leading underscore that can be programmatically referenced.
- The compiler generates a backing field that is accessible via reflection
- The compiler generates a code that will store the information separately from the instance to ensure its security.
38. When using an implicitly typed array, which of the following is most appropriate? Answers:
- All elements in the initializer list must be of the same type.
- All elements in the initializer list must be implicitly convertible to a known type which is the actual type of at least one member in the initializer list
- All elements in the initializer list must be implicitly convertible to the common type which is the base type of the items actually in the list
- There are no restrictions on the items in the initializer list as the array is not declared to be a specific type.
39. Which of the following characteristics is present in the DateTime type?Answers:
- It always references the UTC (GMT) time
- It always references the Local time
- It contains a member indicating which time zone it refers to
- It contains a member indicating whether the time is UTC, Local, or Unspecified
40. Which of the following code samples show a valid static constructor?Answers:
- class Sample { public static Sample() { } }
- class Sample { static Sample() { } }
- class Sample { static Sample(int value) { } }
- class Sample { static void Sample() { } }
41. Which of the following are true regarding System.Web.Mail and System.Net.Mail namespaces? Answers:
- System.Web.Mail is not supported under version 3.5 of the Framework
- System.Web.Mail is deprecated under version 3.5 of the Framework, and it is officially recommended that System.Net.Mail be used.
- System.Web.Mail is the preferred solution when using IIS hosted applications
- There are no functional differences; the items were moved to a new namespace to reflect their applicability in a better way
42. In which of the following ways do structs differ from classes? Answers:
- Structs can not implement interfaces
- Structs cannot inherit from a base struct
- Structs cannot have events interfaces
- Structs cannot have virtual methods
43. To which of the following do automatic properties refer? Answers:
- You declare (explicitly or implicitly) the accessibility of the property and get and set accessors but do not provide any implementation or backing field
- You attribute a member field so that the compiler will generate get and set accessors
- The compiler creates properties for your class based on class level attributes
- They are properties which are automatically invoked as part of the object construction process
44. Given the code below, which of the following items will cause a compilation error? static void F1(params int [] y) { } static void Sample() { int [] j = new Int32[3]; List k = new List(); // ANSWER GOES HERE } Answers:
- F1(j);
- F1(k);
- F1(1, 2, 3);
- F1(new [] {1,2,3})
- None of the above
45. Which of the following are true about Nullable types? Answers:
- A Nullable type is a reference type.
- A Nullable type is a structure.
- An implicit conversion exists from any non-nullable value type to a nullable form of that type.
- An implicit conversion exists from any nullable value type to a non-nullable form of that type.
- A predefined conversion from the nullable type S? to the nullable type T? exists if there is a predefined conversion from the non-nullable type S to the non-nullable type T
46. For which of the following scenarios does Reflection.Emit provide support? Answers:
- Defining methods dynamically.
- Defining types dynamically
- Defining assemblies dynamically
- Defining Instances dynamically
- Exporting an executable code to a disk based assembly
47. Which of the following are true about System.Security.Cryptography under version 3.5 of the framework Answers:
- None of the implementations are FIPS-certified
- Support is provided for the “Suite B” set of cryptographic algorithms as specified by the National Security Agency (NSA) .
- Cryptography Next Generation (CNG) classes are supported on XP and Vista systems
- The System.Security.Cryptography.AesManaged class allows custom block size, iteration counts and feedback modes to support any the Rijndael based encryption.
48. Custom non-fatal exceptions should be derived from: Answers:
- ApplicationException
- DataMisalignedException
- ExecutionEngineException
- SystemException
49. class Sample { public Sample(int x) { } } In the above code, which of the following other class constructors can directly access the provided constructor? Answers:
- public Sample() : this(1) { }
- public Sample() : Sample(1) {}
- Both of the above
- One class constructor can not directly access another constructor
50. Which of the following are characteristics of the System.Threading.Timer class? Answers:
- The method provided by the TimerCallback delegate will always be invoked on the thread which created the timer.
- The thread which creates the timer must have a message processing loop (i.e. be considered a UI thread)
- The class contains protection to prevent reentrancy to the method provided by the TimerCallback delegate
- You can receive notification of an instance being Disposed by calling an overload of the Dispose method.
51. Which of the following is not an unboxing conversion? Answers:
- void Sample1(object o) { int i = (int)o; }
- void Sample1(ValueType vt) { int i = (int)vt; }
- enum E { Hello, World} void Sample1(System.Enum et) { E e = (E) et; }
- interface I { int Value { get; set; } } void Sample1(I vt) { int i = vt.Value; }
- class C { public int Value { get; set; } } void Sample1(C vt) { int i = vt.Value; }
52. Which of the following regarding the System.DateTimeOffset structure are true? Answers:
- It provides an exact point in time relative to the UTC time zone
- It combines a DateTime structure with a TimeZone structure
- It provides arithmetical operations using values with different offsets from the UTC
- It can be used to determine the specific TimeZone for a local time
53. Determining the availability of sufficient memory for an operation can be accomplished by: Answers:
- There is no supported application level means to determine if a specific amount of memory is available.
- using static methods of System.Runtime.MemoryFailPoint and checking the return value
- creating an instance of System.Runtime.MemoryFailPoint and monitoring for an InsufficientMemoryException
- creating an instance of System.Runtime.MemoryFailPoint and monitoring for an OutOfMemoryException
54. When using version 3.5 of the framework in applications which emit a dynamic code, which of the following are true? Answers:
- A Partial trust code can not emit and execute a code
- The generated code has no more permissions than the assembly which emitted it.
- It can be executed by calling System.Reflection.Emit.DynamicMethod( string name, Type returnType, Type[] parameterTypes ) without any special permissions
- None of the above
55. Which of the following characteristics are found in a query expression?Answers:
- It must begin with a from clause
- It must begin with a select clause
- It can end with a group clause
- An orderby clause may optionally follow a select clause
56. When using the Demand method of System.Security.IPermission, which of the following will occur? Answers:
- The permissions of the code which invoked the Demand method will be evaluated.
- For permissions which do a stack walk, an exception will occur only if NONE of the calling codes has the required permission
- For permissions which do a stack walk, an exception will occur if ANY of the calling codes does not have the required permission
- The permission levels of individual stack frames are always checked regardless of the permission type.
57. Which of the following characteristics do classes in the System.Drawing namespace such as Brush,Font,Pen, and Icon share? Answers:
- They encapsulate native resource and must be properly Disposed to prevent potential exhausting of resources.
- They are all MarshalByRef derived classes, but functionality across AppDomains has specific limitations.
- You can inherit from these classes to provide enhanced or customized functionality
- They are Value Type objects.
58. Which of the following are true regarding event declaration in the code below? class Sample { event MyEventHandlerType MyEvent; } Answers:
- MyEventHandlerType must be derived from System.EventHandler or System.EventHandler<TEventArgs>
- MyEventHandlerType must take two parameters, the first of the type Object, and the second of a class derived from System.EventArgs
- MyEventHandlerType may have a non-void return type
- If MyEventHandlerType is a generic type, event declaration must use a specialization of that type.
- MyEventHandlerType cannot be declared static
59. Which of the following statements apply to developing .NET code, using .NET utilities that are available with the SDK or Visual Studio? Answers:
- Developers can create assemblies directly from the MSIL Source Code.
- Developers can examine PE header information in an assembly.
- Developers can generate XML Schemas from class definitions contained within an assembly.
- Developers can strip all meta-data from managed assemblies.
- Developers can split an assembly into multiple assemblies.
60. Which of the following is true about C# generics? Answers:
- C# allows non-type template parameters
- C# supports explicit specialization
- C# allows the type parameter to be used as the base class for the generic type
- C# allows a generic type parameter itself to be a generic
- C# enforces that all codes are valid for all types of parameters
61. The output generated by the fo
llowing code will be: string t = “This Is a Test”; t.Replace(“T”, “?”);Console.WriteLine(t); Answers:
- ?his Is a ?est
- ?his Is a ?es?
- This Is a Test
- ?his Is a Test
62. Which of the following are true about anonymous types? Answers:
- They can be derived from any reference type.
- Two anonymous types with the same named parameters in the same order declared in different classes have the same type.
- Anonymous types can have methods
- All properties of an anonymous type are read/write
63. Which of the following are true regarding multiple versions of an assembly? Answers:
- When multiple versions of an assembly are available on the search path (AKA private assemblies), the runtime will use the first matching assembly with a version number equal to or higher than the assembly version that was originally linked against.
- When assemblies are resolving in the GAC (AKA shared assemblies), both the originator and the version are considered in determining the appropriate assembly.
- Configuration files can be used to override the version specified at build time.
- Strong Names are not required to utilize .NET’s versioning capabilities
64. Which of the following are true about declarative attributes? Answers:
- They must be inherited from the System.Attribute.
- Attributes are instantiated at the same time as instances of the class to which they are applied.
- Attribute classes may be restricted to be applied only to application element types.
- By default, a given attribute may be applied multiple times to the same application element.
65. Which of the following statements are applicable to LINQ to SQL?Answers:
- It is an O/RM (object relational mapping) implementation.
- It is a set of enhancements to the DataSet and DataTable classes.
- It requires the use of the SQLServer as the database
- Because LINQ is based on Queries, it can not be used to modify the data in the database.
- None of the above
66. When Implementing System.EnterpriseServices.ServicedComponent derived classes, which of the following statements are true? Answers:
- Enabling object pooling requires an attribute on the class and the enabling of pooling in the COM+ catalog.
- Methods can be configured to automatically mark a transaction as complete by the use of attributes.
- You can configure authentication using the AuthenticationOption when the ActivationMode is set to Library.
- You can control the lifecycle policy of an individual instance using the SetLifetimeService method.
Finally no more words require about the DOT NET 3.5 USING C# TEST information in this session of this content. If you are require knowing more, Please ask to us via our contact us form or comment box. Please make sure that you don’t send Personal information via the Comment box. Thank you for being with us.

ReplyDeleteHi admin, i went through article. As we all know, .net is most popular programming language and it offer huge career prospects for talented professionals. It’s totally awesome, keep on updating your blog with such awesome information. .Net Training in Chennai|DOT NET Training in Chennai